Segregation of Duties Conflict Detection
Automated detection of SoD conflicts in SAP and any ERP. Identify conflicting access rights that could lead to fraud or errors through comprehensive Segregation of Duties analysis across roles and user assignments. Learn about SoD
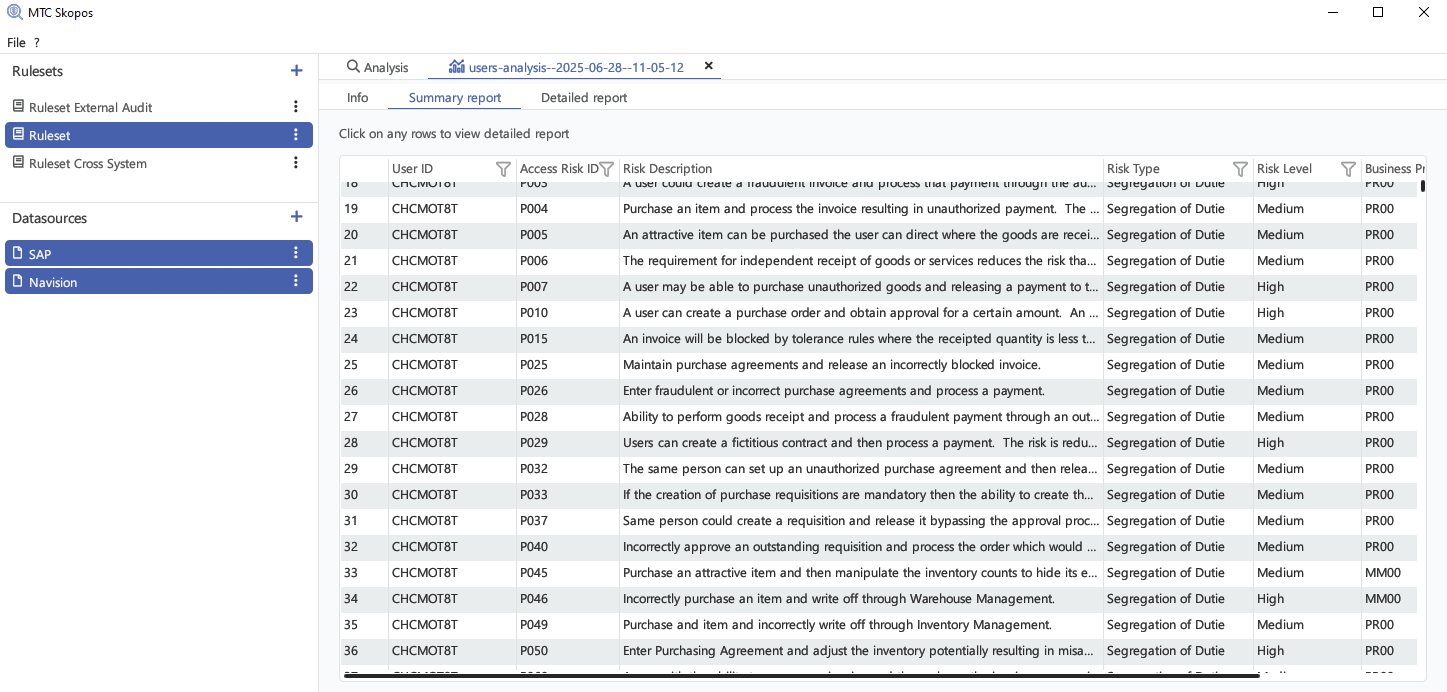
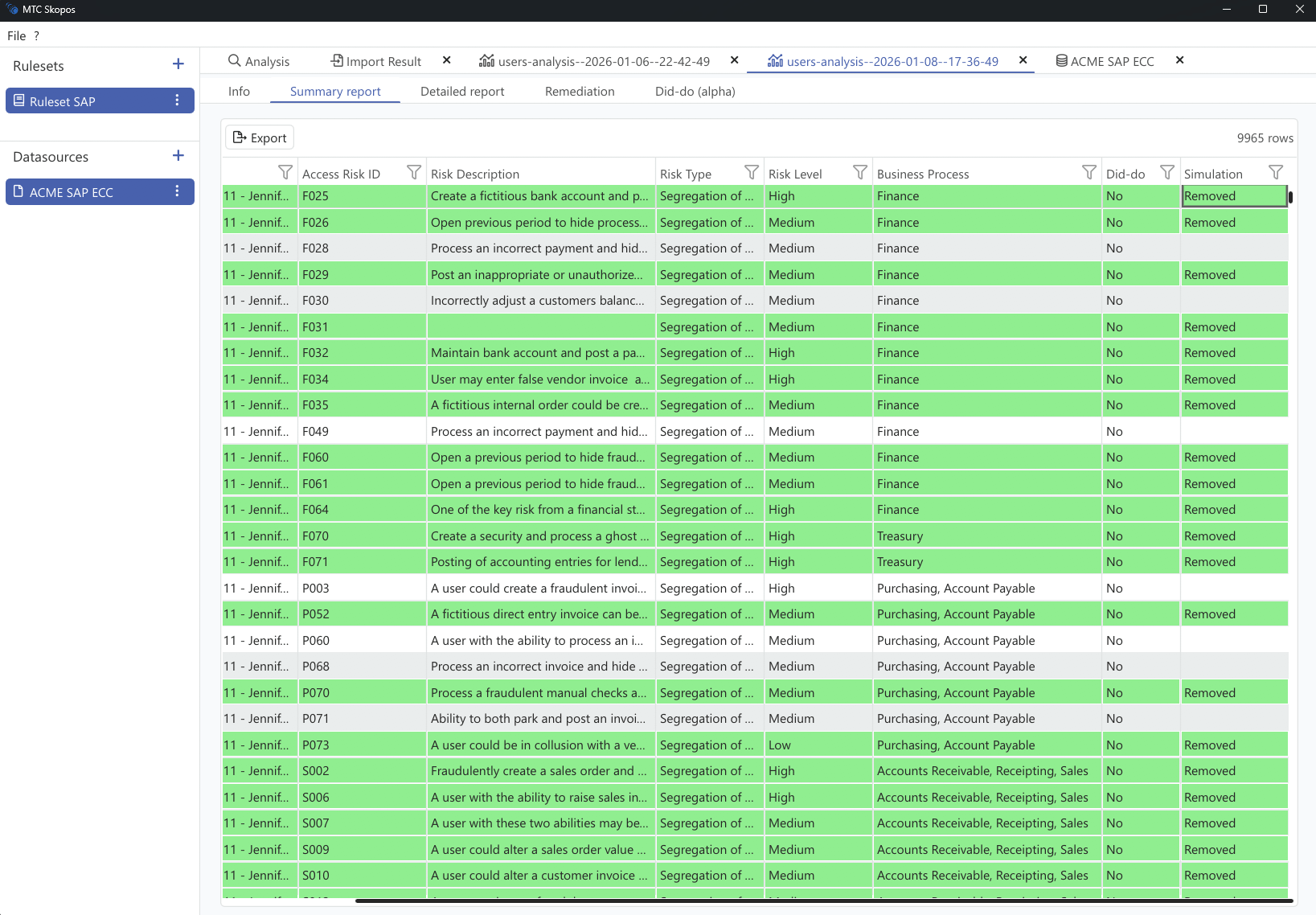
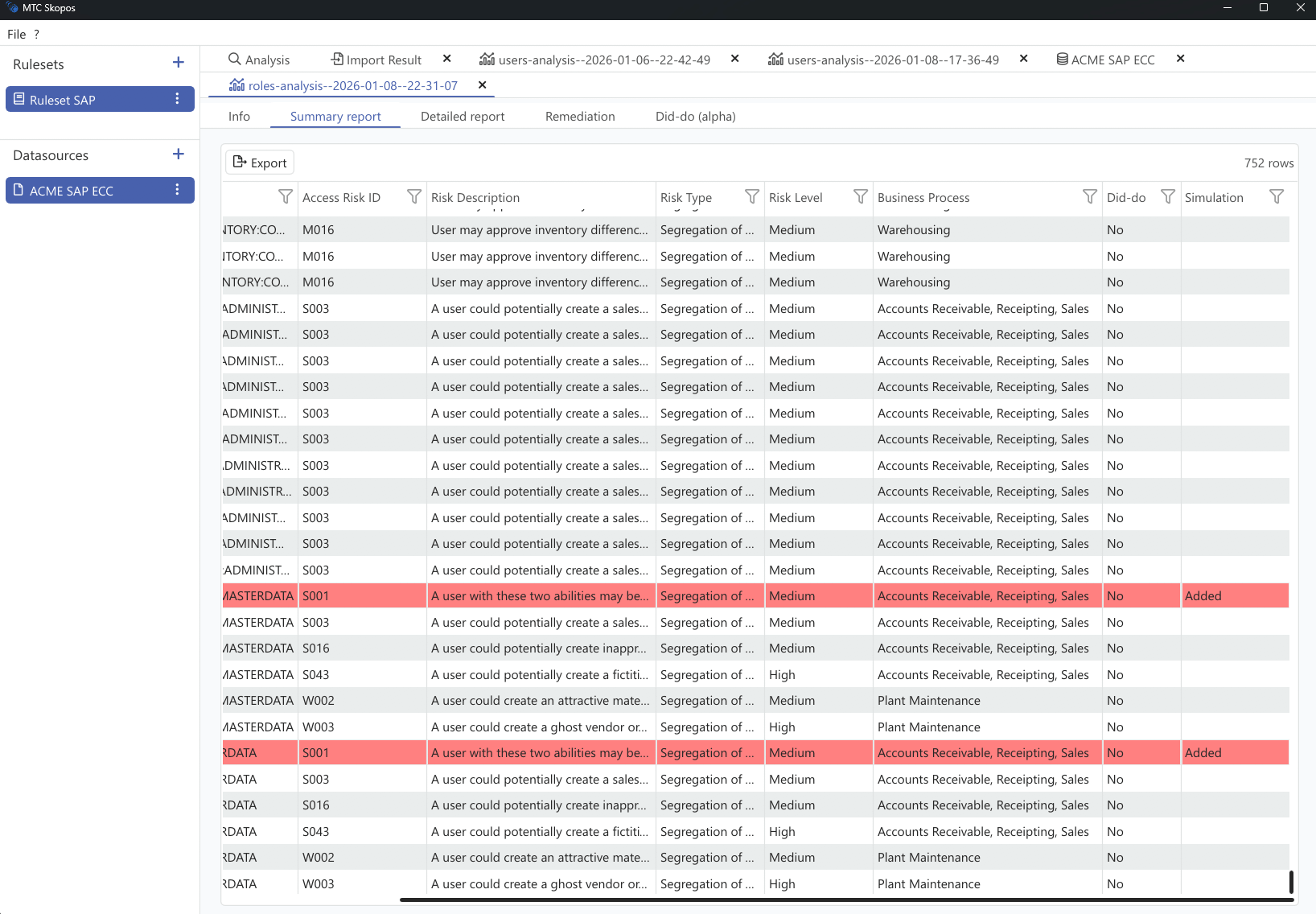
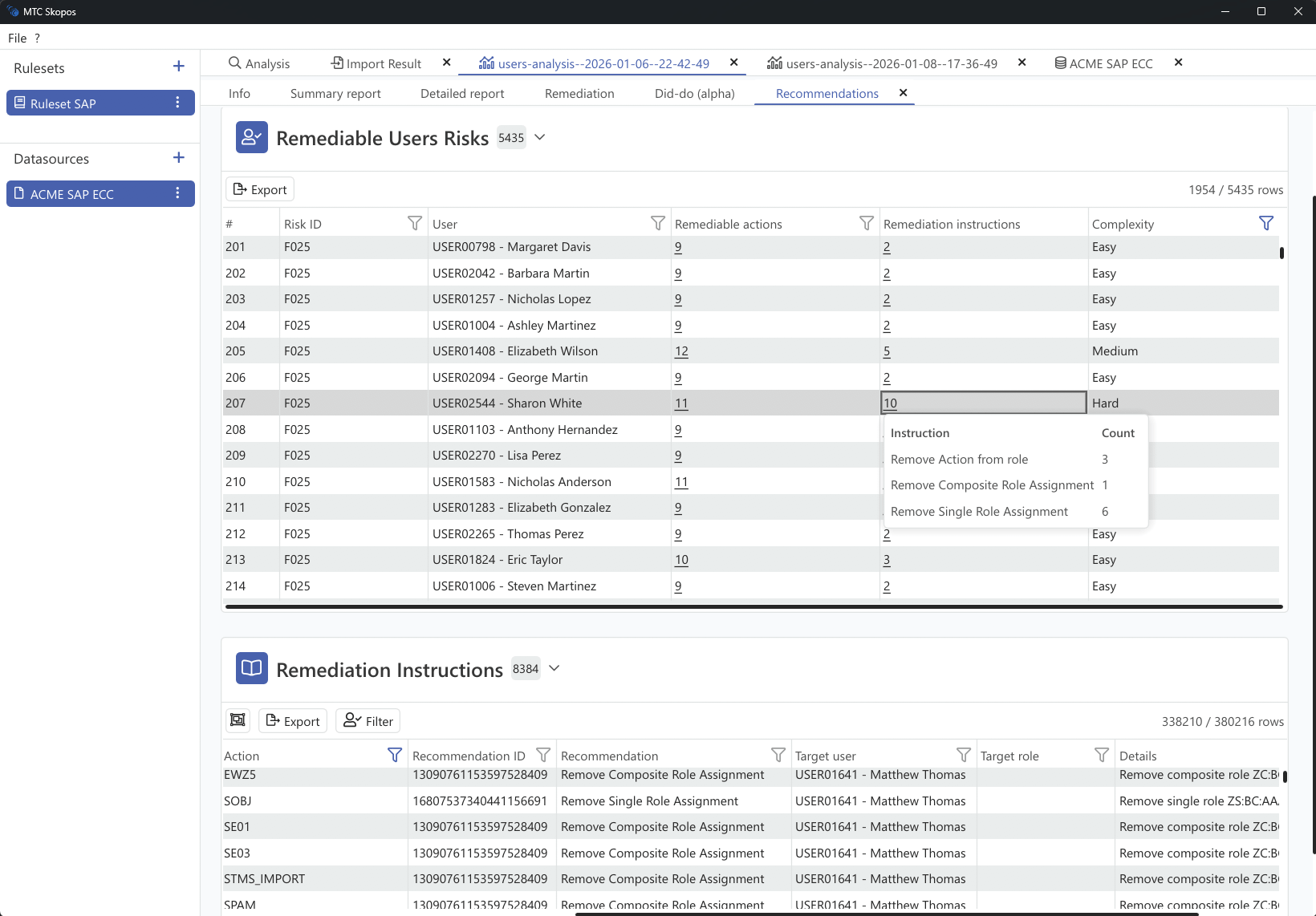
Users and roles analysis
Analyze access risks with precision whether by role or user.
MTC Skopos helps you uncover hidden
conflicts, overprovisioning, and potential compliance breaches while optimizing
your license costs by estimating the FUE impact of your users and roles.
Cross-System Risk Detection
Assess risks arising from access across multiple systems, and identify critical
combinations that
span different platforms.
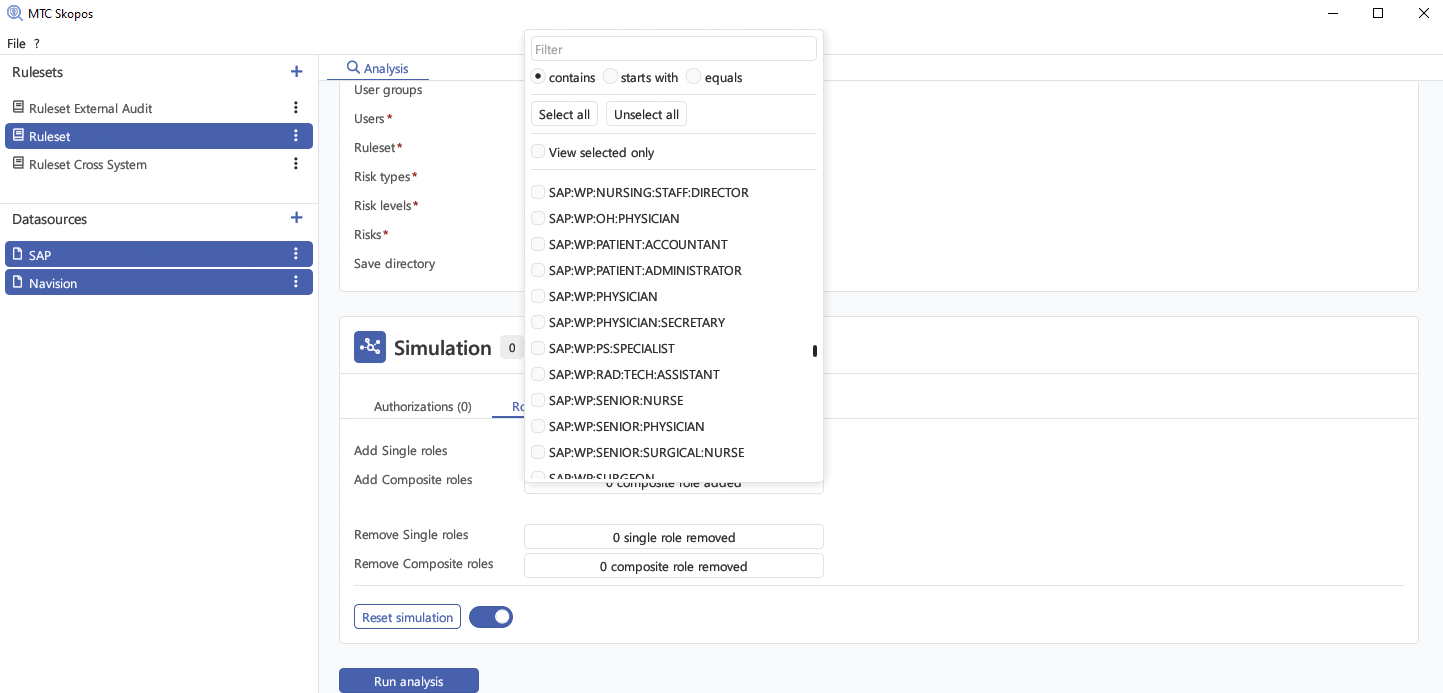
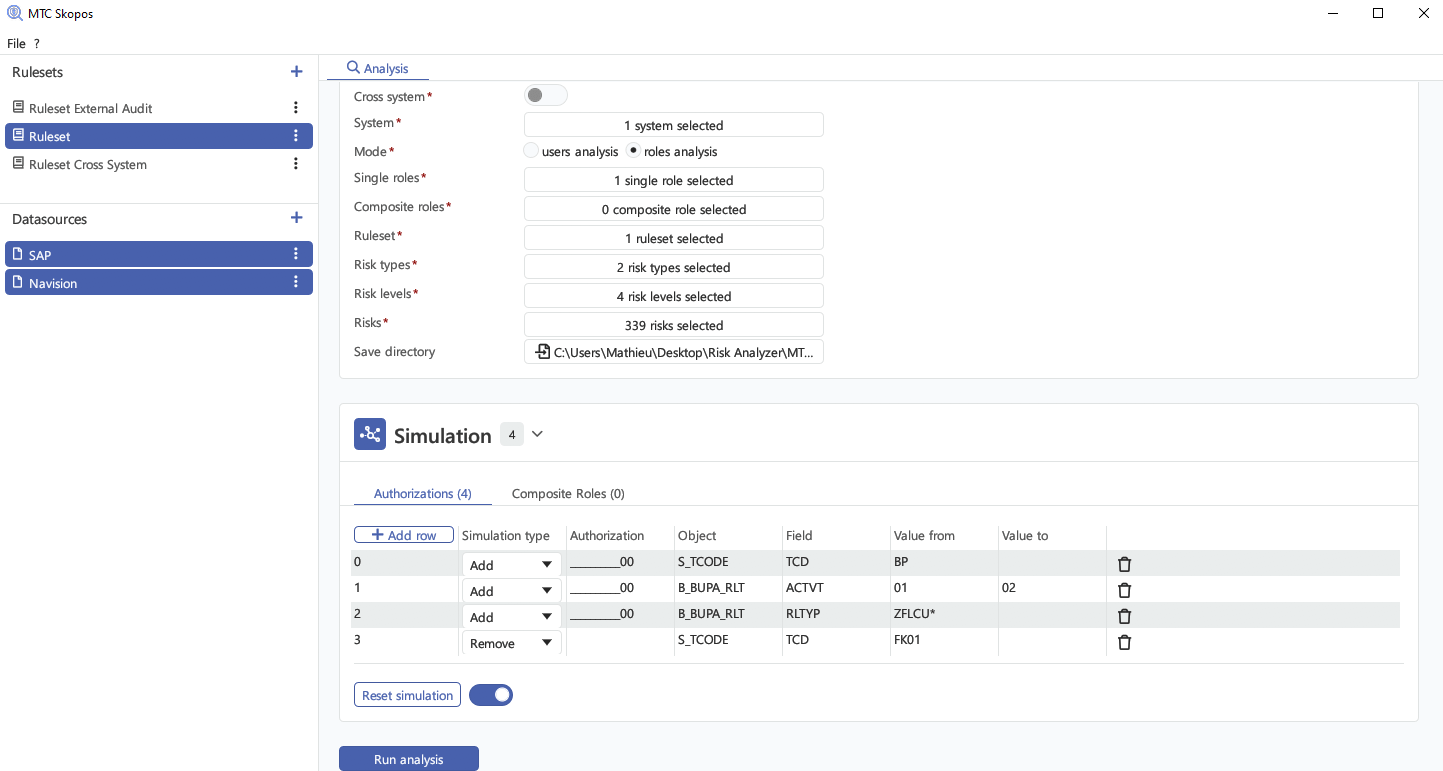
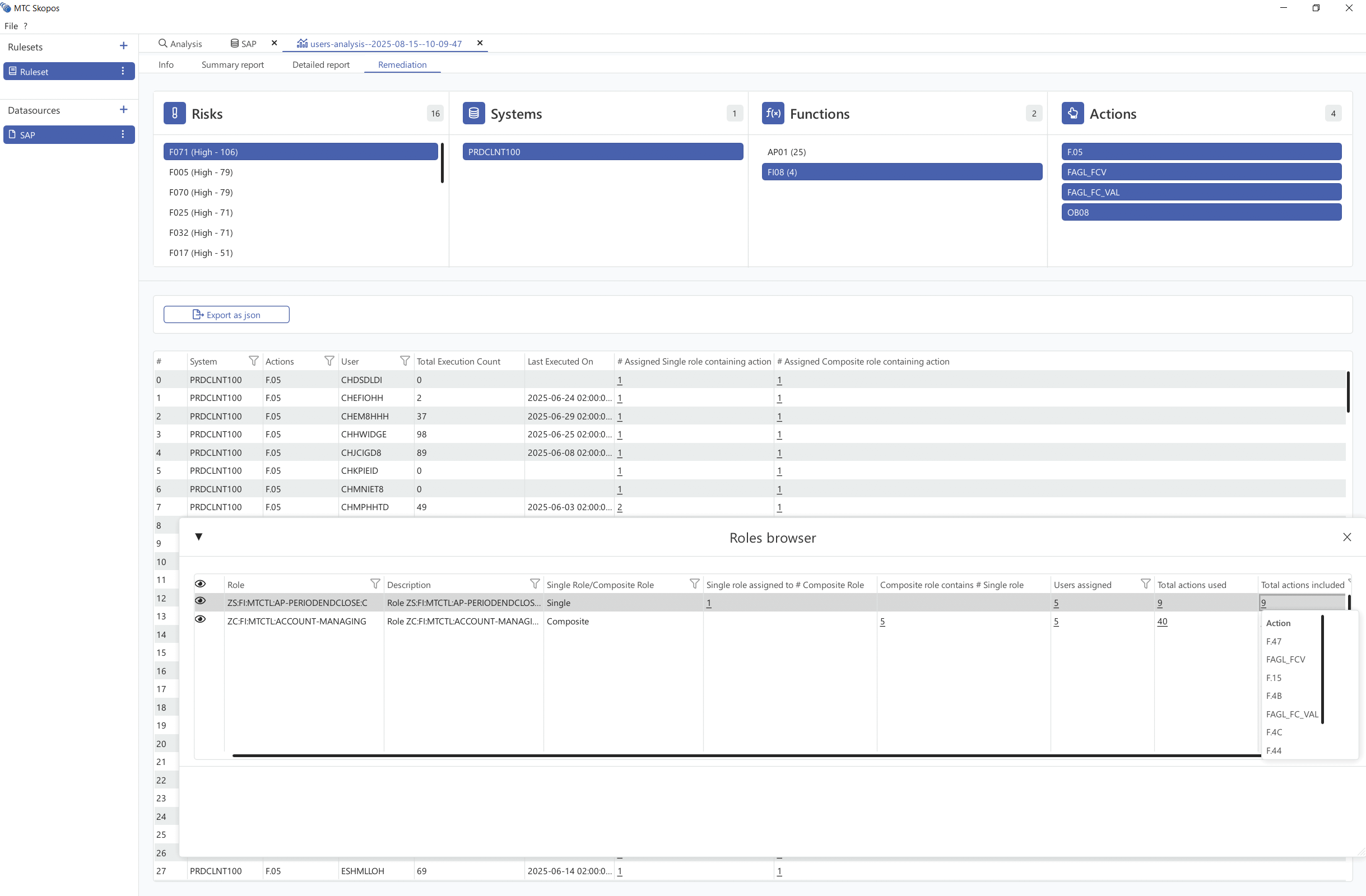
Permission Simulation
Test role and authorization changes before applying them to production using simulation
feature.
See exactly how changes will impact user access and identify potential security
risks.
Simulate with Confidence:
- Adding or removing user role assignments
- Adding or removing authorization within existing roles
- Creating new role
- Cross-system access combinations and their security implications
Preview, validate, then deploy - ensuring every access change enhances security rather than creating
vulnerabilities.
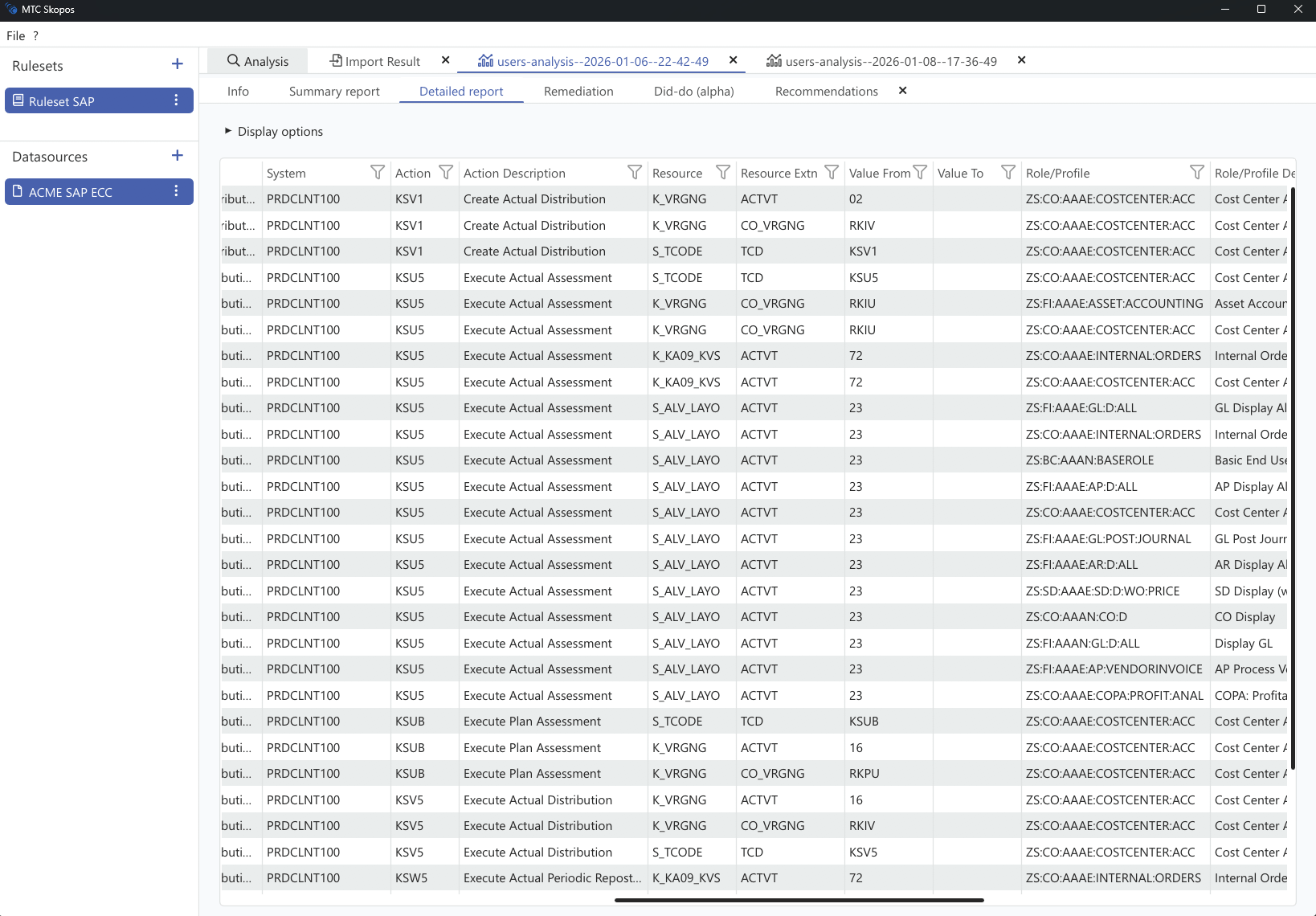
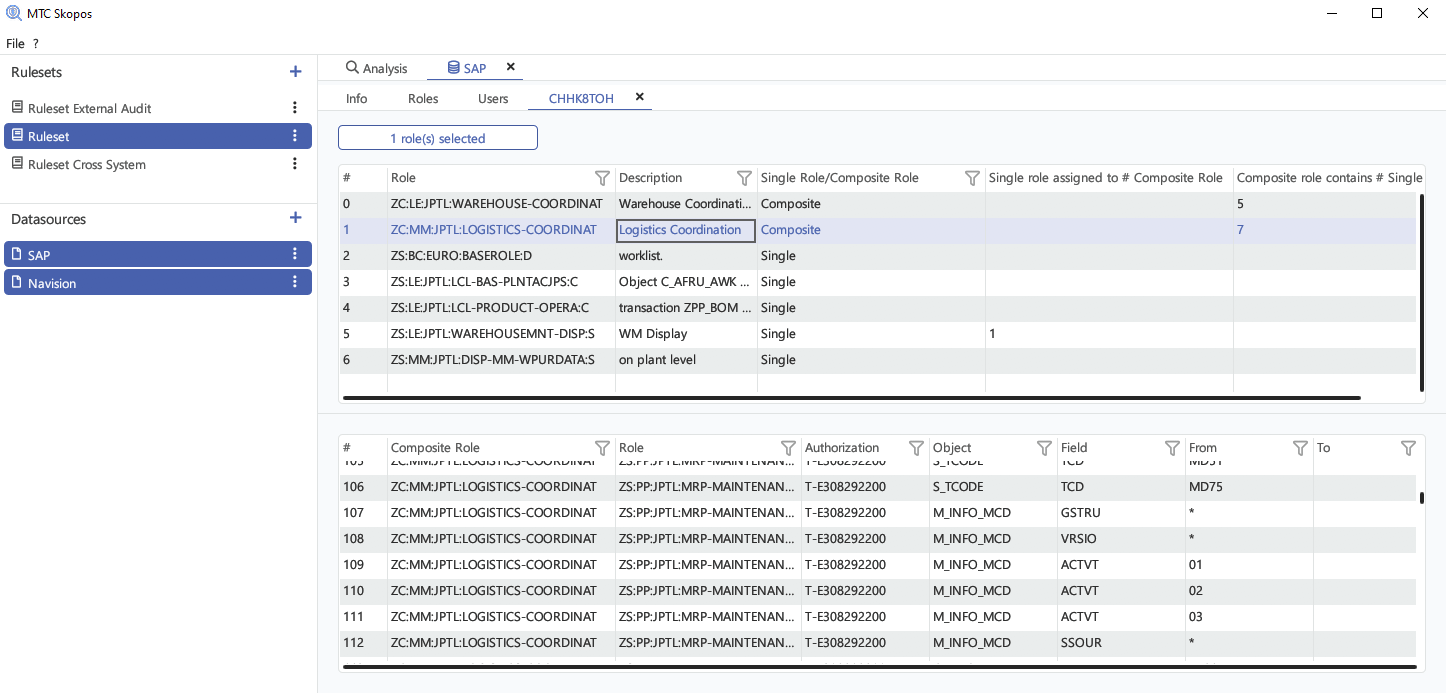
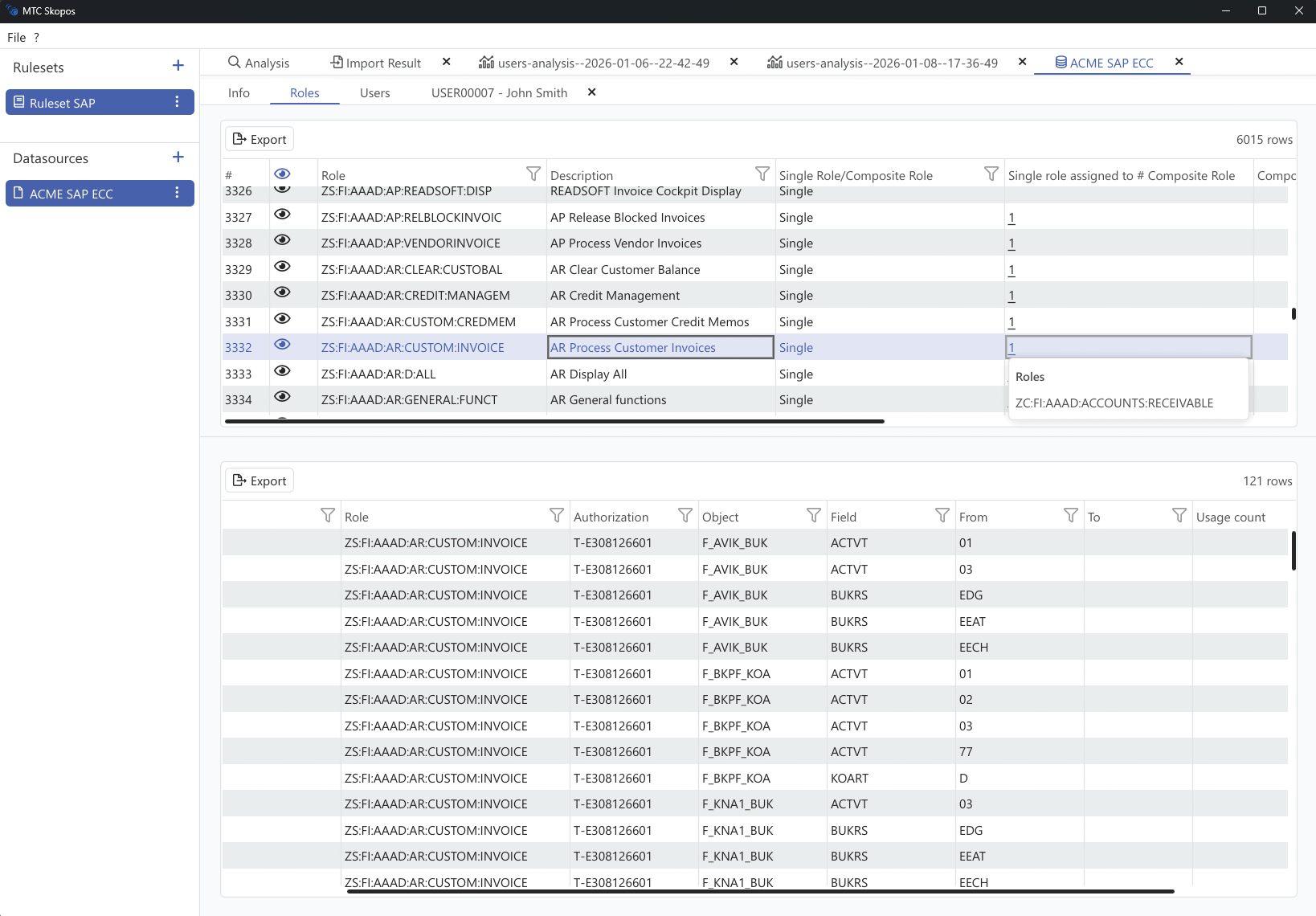
User & Role Explorer
Easily navigate your authorization concept. Review user access and role configurations with intuitive
interface.
Even if system contains huge amount of data, MTC Skopos remains fast and smooth.
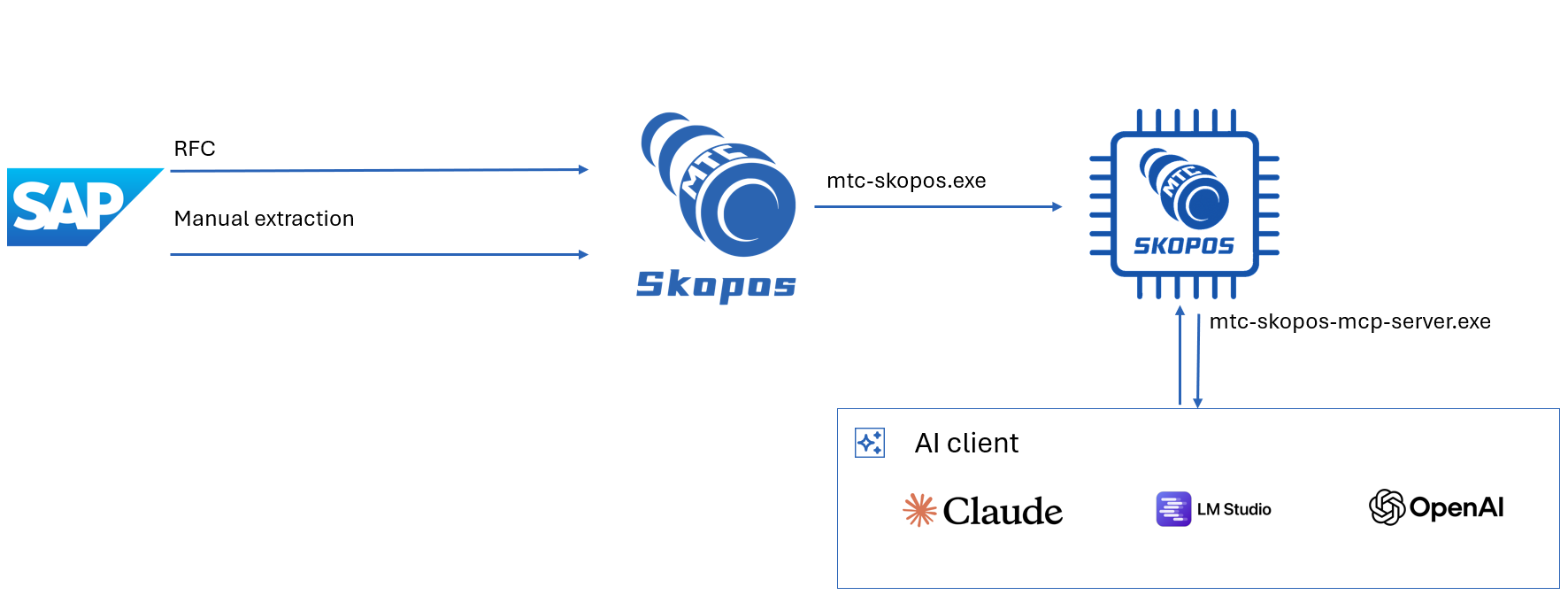
MCP-Powered AI Agents
A conversational AI interface that leverages Model Context Protocol (MCP) to connect with specialized AI agents, allowing you to query your access risk analysis results using natural language and receive intelligent insights in plain English. Read about MCP integration
*Data confidentiality varies by AI deployment: on-premises/local models maintain full privacy, while cloud-based AI services may process your access risk data externally
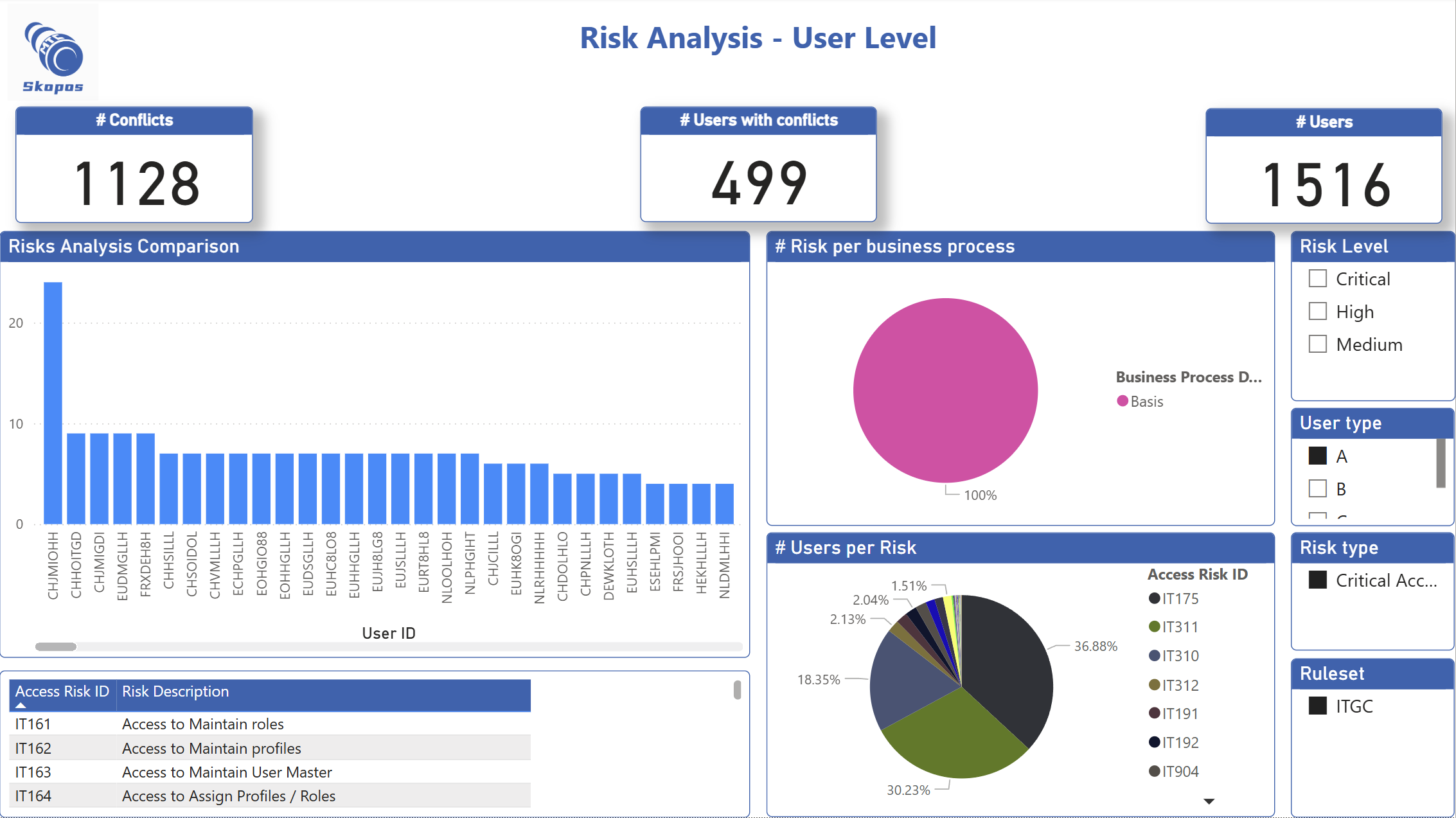
Executive reporting
We provide Ready-to-use Microsoft PowerBI report (.pbix) with actionable insights. Transform risk analysis results into
Business-oriented insights and comprehensive reports to support informed decision-making at the
executive level. See reporting capabilities
High-Performance Engine
Reduce cost thanks to an ultra-fast analysis.
Obtain report for a single user analysis in a second and a complete system
analysis in minutes
not hours.
In combination with simulation feature, it is possible to quickly iterate over role
provisioning. Why we built this
Privacy
MTC Skopos is a local desktop application which does not connect to internet*.
There is no telemetry nor user tracking system. Your data stay on your computer.
*Some feature such as integration with SAP RFC requires internet connection, but most of
time MTC Skopos works offline.
Export Data in Open Formats
True Data Ownership
Export your Segregation of Duties analysis, Critical Access reports, and computed statistics in universally compatible formats.
No vendor lock-in, unlike competitors who lock your critical compliance data behind proprietary formats or complex database structures, MTC Skopos empowers you with instant data portability through industry-standard JSON and CSV exports.
AI-Ready Data Structure
Our intelligently formatted exports are optimized for AI and machine learning tools. We've pre-processed and structured the data to minimize token consumption, reducing your AI processing costs as much as we can.
Instant Integration with Your Analytics Stack
Whether you're using Power BI, Tableau, Python, R, or emerging AI analytics platforms, our clean JSON/CSV exports integrate seamlessly.
Remediation Reports
Leverage usage data to identify remediation opportunities and determine a step-by-step technical action plan whilst preserving business operations. Learn about AI remediation
Advanced Remediation
Automated Segregation of Duties conflict resolution for SAP and any ERP. Algorithmic recommendations adapt to your criteria, delivering personalized remediation strategies for SoD conflicts based on your risk parameters and organizational priorities. How it works
SAP Role Designer (AI)
Describe your requirements to our AI and automatically generate optimal role designs with default authorization configurations.
Did-Do Analysis
Determine if access risks were actually exploited by inspecting change documents and identifying impacted data. Essential for accurate risk mitigation when no remediation is possible.